I know that some of you are expecting a post similar to that about a toothbrush botnet, but this is not a hypothetical case. It actually happened.
A Malwarebytes Premium customer started a thread on Reddit saying we had blocked malware from trying to infect their computer after they connected a vibrator to a USB port in order to charge the device.
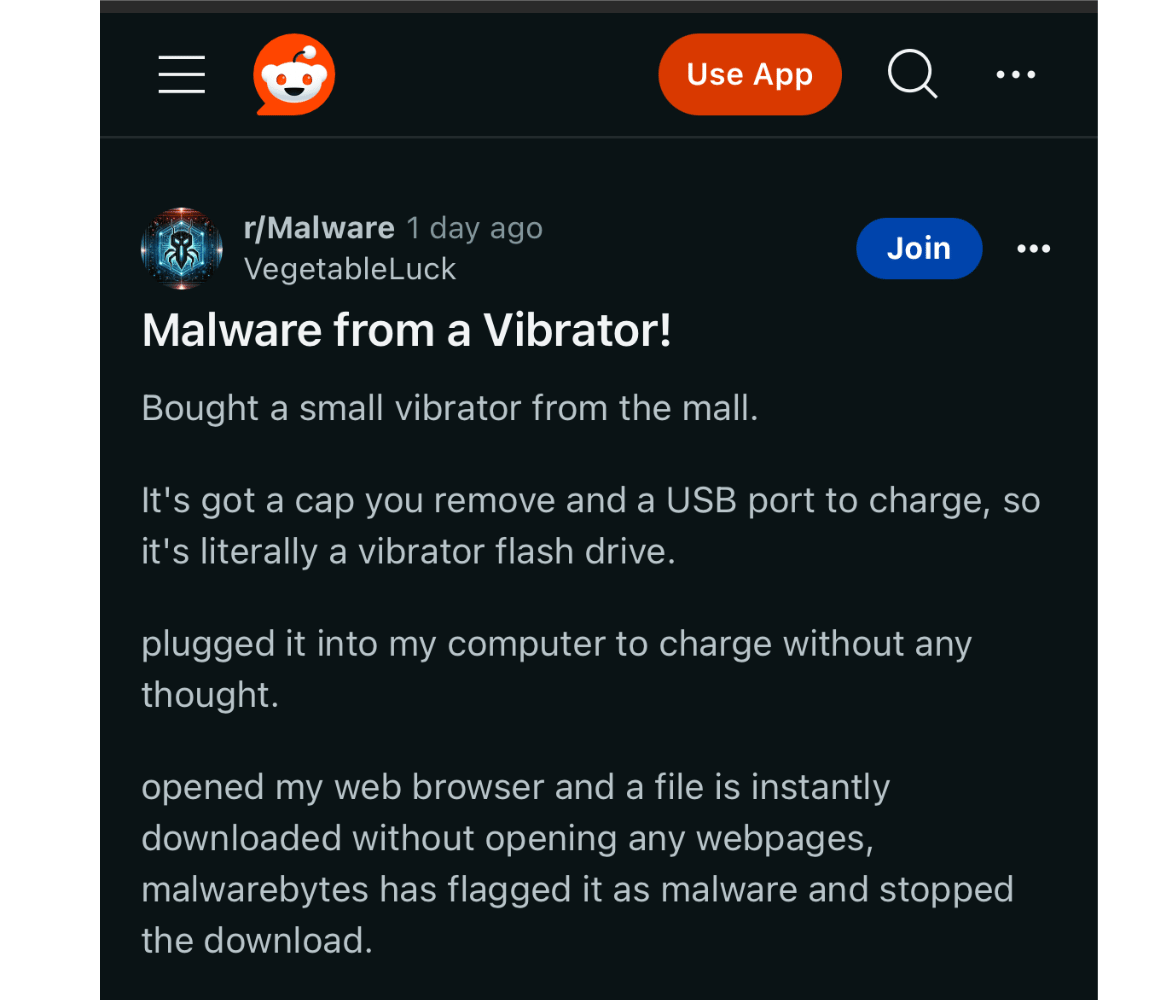
The vibrator, Spencer’s Sexology Pussy Power 8-Function Rechargeable Bullet Vibrator, was infected with an information stealer known as Lumma.
Lumma is available through a Malware-as-a-Service (MaaS) model, where cybercriminals pay other cybercriminals for access to malicious software and its related infrastructure. Lumma steals information from cryptocurrency wallets and browser extensions, as well as two-factor authentication details. Lumma is often distributed via email campaigns, but nothing stops the cybercriminals from spreading it through infected USB drives, as is the case here.
The question that remains is, how did the vibrator get infected? The victim bought the vibrator at Spencer’s, so we reached out to the company in an attempt to get to the bottom of this.
Spencer’s acknowledged that it was aware of the problem, but the team investigating the issue was unable to provide further information at this point. We’ll keep you updated if we receive word from them or find out any more information ourselves.
Update February 28, 2024
A spokesperson for Spirit Halloween/Spencer’s reached out asking us to add their official statement:
“We are aware of the issue raised regarding one of our intimate products and can confirm that it is unable to transmit data, as there is no physical connection from the PC board circuitry to the USB data pins.“
This definitely makes sense for a device that is not capable of reprogramming by the user. It basically means the device does not need to be connected with a USB condom.
Our advice when it comes to USB devices, including rechargeable vibrators:
- Don’t connect the USB to your computer for charging. If you use a good old-fashioned AC plug socket then no data transfer can take place while you charge.
- If you still want the option to connect via USB, USB condoms or “juice-jack defenders” as they are sometimes called will prevent accidental data exchange when your device is plugged into another device with a USB cable.
- Treat untrusted devices like you would the “lost USB stick” in the parking lot. You know you shouldn’t connect those to your computer, right?
- Always use security software. In this case, the customer was protected by Malwarebytes Premium. If they weren’t using security software, their personal information might have ended up in the hands of cybercriminals.
Technical details
The customer was kind enough to provide us with the content of the flash drive. On it were a host of XML files and a Microsoft Software Installer file (Mia_Khalifa 18+.msi).

The XML files all look very similar to the above and seem to be designed to functions as an XML bomb. An XML bomb is an exponential entity expansion attack, similar to a ZIP bomb, that is designed to crash the web application. This is likely used to draw the attention of the victim away from the actual malware.
The installer creates a program entry called Outweep Dynes.
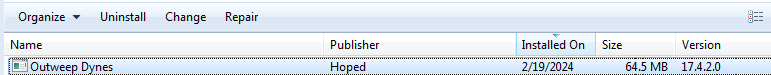
The Outweep Dynes “program” is yet another installer dropped in %USERPROFILE%\AppData\Local\Outweep Dynes\InstallerPlus_v3e.5m.exe
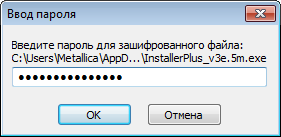
To hinder reverse engineering, extraction of the executable is password protected. But with the password hardcoded in the file, that was not a problem.
The file then executes a heavily obfuscated portable executable detected by Malwarebytes as Trojan.Crypt.MSIL which is Malwarebytes’ generic detection name for a type of obfuscated Trojan programmed in Microsoft Intermediate Language (MSIL).
The dropped executable is a combination of the Lumma Stealer and an additional .NET dll library.
Malwarebytes ThreatDown customers enjoy protection by Advanced Device Control. When a USB device is connected, ThreatDown now doesn’t just control access—it actively scans it. You can also now choose to block the device until the system scans it. This means threats are stopped in their tracks, well before they can do any harm.
IOCs
Program name:
Outweep Dynes
Folder:
%USERPROFILE%\AppData\Local\Outweep Dynes
Filenames:
InstallerPlus_v3e.5m.exeInstaller-Advanced-Installergenius_v4.8z.1l.exe
SHA256 hashes:
- 207ee8fb2a824009fe72a857e041297bde3b82626b8883bc05ca8572b4dd148a
- e0f4382f4534c2c0071ce0779d21f0fed59f428cdb622b1945e0a54157c19f95
- be6efe16701cb69ec6e48441a6ad1c1f934e0f92878ccdfafc3f52cbc97be5c2
Vibrator:
Spencer’s Sexology Pussy Power 8-Function Rechargeable Bullet Vibrator
We don’t just report on threats—we remove them
Cybersecurity risks should never spread beyond a headline. Keep threats off your devices by downloading Malwarebytes today.













